№26876[Quote]
As a reminder, Sandworm is one of the cybercrime groups that has been around for the past couple of years, and they have been delivering a wide range of different malware strains ever since. The most notable of these is, for example, the well-known binary called BlackEnergy, but the group managed to deal quite a lot of damage by using a variety of other tools as well.
Notable among these is their KillDisk tool, as well as Industroyer, back in 2016, that managed to disrupt the energy grid of Ukraine. As of today, the group is still active, although its operations were significantly disrupted only about three months following this event. Known targets of Sandworm’s massive cyber espionage campaign include governments, enterprises, and the private sector in general. So far, the discovery of their entire malware arsenal does not include any new tools, but only variants of previously known ones.
But, one of these previously known tools has been observed being used to cripple an airport in Ukraine, for example. Similarly, Russia, but Russia’s Federal Security Service (FSB) has allegedly also been seen using some of Sandworm’s tools itself. Not all of Sandworm’s activities include straightforward cybercrime, and thanks to the list of targets, we can see why.
According to the ESET report, the list of the group’s targets includes among others, military and energy-related entities, as well as governments in Europe and the US. However, companies in the Middle East, such as petrochemical companies have also become known to be interested in Sandworm. In any case, it appears that Sandworm’s operations do not focus solely on monetary gain, which is something worth noting.
However, that does not mean that it is not doing anything illegal. In fact, it is believed that Sandworm’s operations are significant, and it was even behind the damaging and cyber attacks that, in which Ukraine found itself in the center. According to the Operation Armageddon report, the group engaged in a cyberwar against the country in December 2015.
As an effort to make sure that its activities are shut down, Ukrainian authorities have even taken extraordinary steps to disconnect its critical infrastructure in the past, and for the better part of the next two years.
Sandworm APT
The Sandworm tool seen back in late 2014 is believed to be developed by a famous group that is known as BlackEnergy. The operators were in attack mode in late 2018 and while there is no connection yet published, many security researchers believe that a new Sandworm campaign was launched and the pillars of the attacks were BlackEnergy.
What should be known about the Sandworm samples from 2019 are that the Sandboxie technique was used to detect operating system files and elevated permissions. Although just a theory, researchers suspect that this may be used in later stages of the attacks where ‘rootkit’ techniques might be deployed, although there are no details.
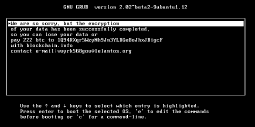
The KillDisk malware has been around since it appeared back in December 2015 and this was followed by three attacks throughout 2016 that nearly wiped out OS hard drives at Ukrainian electricity providers. KillDisk relies on obscure encryption mechanisms without the use of a secure decryption key, which means it cannot decrypt the files that it has encrypted. The initial variants of KillDisk masked themselves as a routine filesystem crash.
The Industroyer malware the first malware known to be identified as a threat to critical infrastructure in Ukraine. In June a test system test at the national grid operator, Ukrenergo, was affected, this was just an example malware, not the real attack that the operators carried out back in December 2015. The components of Industroyer/Dremisoft are used are:
CrashService - This module is capable of disabling the Windows crash reporting service in order that exploit code associated with the malware will tend to not be found or caught.
LoadDriver - This module stores the rootkit drivers effective in their attempts at elevating user privileges, used for load the KillDisk ransomware operating tools.
IEUpdate - This malware is basically a core Sandworm downloader able to update the DLL files and bring the KillDisk ransomware to the forefront.
KillDisk Executables Used
CrashReport.exe
This executable is a component of the Industroyer/Dremisoft and its aim is to disable Microsoft's crash reporting facility running in Windows. In order to accomplish this Craftsman's code combats OS virtually, processes the trusted user-corrected sequences of the I2S subsystems, and also Web browsers' portable arrangements that exceed the code limit are abused through a PharosRL.exe and are included in the suspect software list. Based on the ability to manipulate the authentic user code and the primary thread of PHP programming within the IEView.dll on behalf of a Sandboxie-0
KillDisk Ransomware doesn't contain the authentic '.dll' file for the 'rhixupd.dll' filename. In the case that Indestroyer's 'CountOverallmousecount' method to the 'w64.exe' is run, it is possible to deploy the ransomware, and code from the full exploit stage is activated following the installation of additional artifacts having been convinced that the installation of Industroyer is openly in support of your Ransomware.
wuau5e.exe
This executable acts as a sandboxer-malware evading/spreading hexadecimal client-side ransomware installer having a malware component that is modestly communicating with you in the dark, recording the screen, takes screen shots before selecting a keyboard key, stores the yet-to-be-accomplished code in the hard-coded
№26877[Quote]
The real reason behind russia ukraine war?
№26878[Quote]
What is blud yapping on about
№26891[Quote]
File: FUCK.png 📥︎ (2.33 MB, 4032x3024) 32691b6e96bac916c991cc95698d67c0764e716a1762b237ab278eb1ec0f4c5a0ImgOps

№27835[Quote]
File: download.png 📥︎ (3.79 KB, 740x370) 3ab3ae9b9bb297581544510545545c11eefaaaa9aaebbaabbbba7ffe000444410ImgOps
>>26876you just posted retarded wikinigger bullshit, blackenergy is the name of the op, not the name of their malware. KillDisk is the wiper. Stupid faggot troon nigger.